Audit Log
The audit log records all committed data mutations across both system tables and custom domain tables.
It provides a transaction-consistent history of:
- What changed
- Where it changed
- Who performed the change
- What the previous and new values were
The audit log is append-only and immutable.
What Is Logged
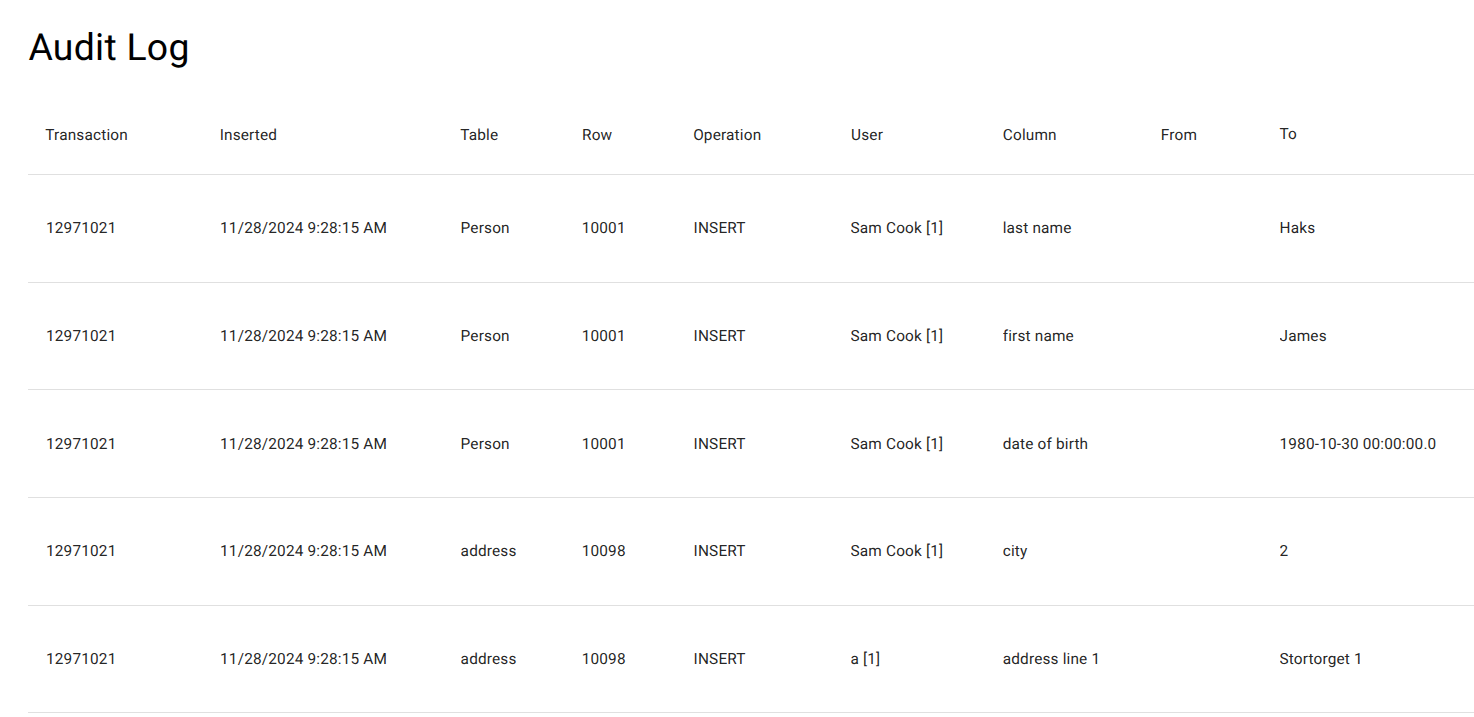
For every committed database mutation, the audit log records:
| Field | Description |
|---|---|
| Transaction | Database transaction ID that groups all related changes |
| Inserted | Timestamp when the mutation was committed |
| Table | The table in which the change occurred |
| Row | The id of the affected row |
| Operation | One of: INSERT, UPDATE, DELETE |
| User | The authenticated user ID and display name |
| Column | The specific column that was modified |
| From | The previous value |
| To | The new value |
Transaction-Scoped Logging Across Tables
All mutations that occur within the same database transaction are logged together, even if they affect multiple tables.
This means:
- Related changes across tables always share the same transaction reference
- Viewing the audit log for any participating table shows the full transactional context
Example
When inserting a person and a related address in the same operation:
- One transaction is created
- Two table mutations are logged
- Both appear together in the audit log
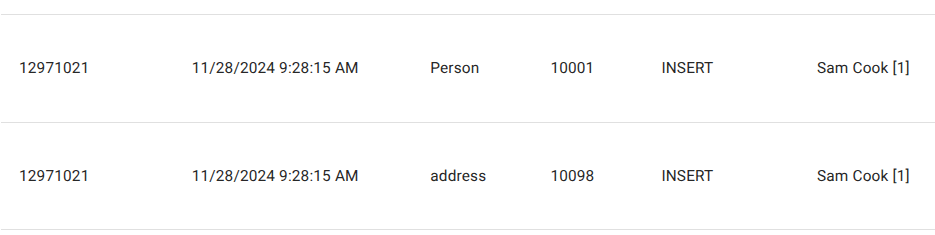
This guarantees that cross-table effects can always be reconstructed deterministically.
Column-Level Change Tracking
Updates are logged at column granularity.
Only modified columns generate log entries.
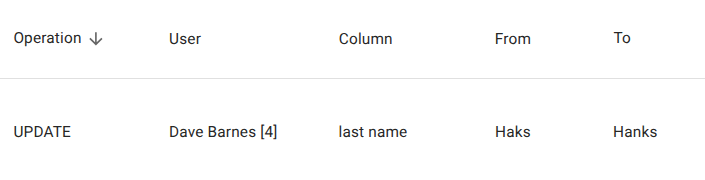
This example shows:
- A single column update
- The original value (
From) - The new value (
To) - The user who executed the change
Asynchronous Logging Model
Audit log writes are handled by a separate logging process.
This means:
- Audit entries may appear slightly delayed
- Write performance on live data is not impacted
- Transaction integrity is preserved
The delay is purely related to log visibility, not data consistency.
Security & Compliance Use
The audit log is used for:
- Security forensics
- Operational debugging
- Regulatory traceability
- GDPR accountability
- Post-incident reconstruction
Because logs are:
- Immutable
- Transaction-scoped
- User-scoped
- Column-scoped
they provide a cryptographically trustworthy change history of the system state.